Data Privacy
Introduction

Data privacy has become a major concern in the digital age. With the rise of the internet and the increasing amount of data being collected, it is more important than ever to protect the privacy of individuals. Nearly every company collects data on its customers, and this data can be used for a variety of purposes, from targeted advertising to improving products and services. However, this data can also be misused, leading to privacy violations and breaches.
For years, companies were gathering petabytes of data on their customers without much thought to privacy or even how they were planning to use it. Data storage was cheap, and the potential benefits of collecting and analyzing this data seemed too great to pass up. However, governments and consumers have become increasingly concerned about data privacy, leading to the introduction of new regulations and laws aimed at protecting individuals' data.
Data Privacy Basics
When working with any user data, it is important to follow best practices to ensure that data is kept secure and private. Your goal should be data protection by design and by default. This means that you should build privacy protections into your software from the beginning and ensure that data is only collected and used for legitimate purposes. No special actions should be required by the user to protect their data.
There are three main components to data privacy:
- Privacy: Are we gathering only the data we need?
- Confidentiality: Are we keeping the data secure?
- Anonymity: Can we separate the data from the individual?
Every company that collects data should have a data privacy policy that outlines how data is collected, stored, and used. This policy should be easily accessible to users and should be written in clear, easy-to-understand language. Users should be able to easily opt out of data collection if they choose to do so.
Types of Data
When thinking about data privacy, it is important to consider the different types of data that you collect and how they should be protected. Each type of data has its own set of rules and regulations that govern how it can be collected, stored, and used. Be sure to track the types of data you are collecting and how it is stored.
Protected Data
There are four main types of protected data:
- Personally Identifiable Information (PII): This includes data that can be used to identify an individual, such as their name, address, phone number, email address, social security number, or driver's license number.
- Protected Health Information (PHI): This includes data that is related to an individual's health or medical history, such as medical records, lab results, or insurance information.
- Personally Identifiable Financial Information (PIFI): This includes data that is related to an individual's financial information, such as bank account numbers, credit card numbers, or income information.
- Student Records: This includes data that is related to a student's educational records, such as grades, transcripts, or disciplinary records.
Non-Protected Data
There are also types of data that are not considered protected, but that should still be handled with care:
- Non-Sensitive PII: This includes data that can be used to identify an individual, but that is not considered sensitive, generally because the data is publicly available.
- Non-Personally Identifiable Information (Non-PII): This includes data that cannot be used to identify an individual. Note that this data can sometimes be combined with other data to identify individuals, so it should still be handled with care.
Categorizing Data
When working with data, it is important to clearly identify and categorize the data based on its sensitivity and the level of protection it requires. This will help you determine the best process for ensuring that the data is kept secure and private. Unfortunately, there is no one-size-fits-all solution for data categorization, as the rules will vary depending on the type of data you are working with and the regulations that apply to your industry. Regional regulations can also have a significant impact on how data is categorized and protected.
Data Privacy Regulations
Each country will have their own data privacy regulations that companies must follow. This can have a significant impact on how companies operate in those regions. The map below shows the area covered by Google Street View in Europe.
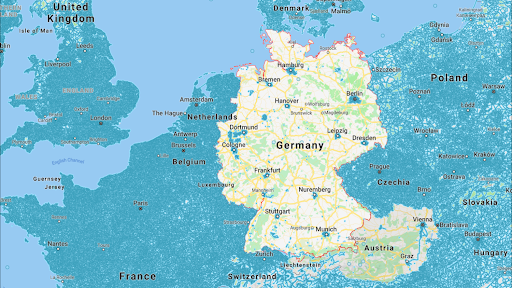
Notice that most of Germany not covered. This is because Germany has strict data privacy laws that prevent Google from collecting and displaying the view from the public streets. The laws in Germany require that individuals give their consent before their data can be collected, and Google has been unable to obtain this consent from enough individuals to create a complete street view map of the country.
When considering data privacy regulations, it is important to be aware of the laws that apply to your industry and the regions in which you operate. Failure to comply with these laws can result in significant fines and penalties, as well as damage to your company's reputation.
There's no way to cover all the data privacy regulations in a single article. Many of them are complex and some are even contradictory. Instead, I'm going to focus on the current US regulations and the General Data Protection Regulation (GDPR) in Europe.
US Regulations
Privacy laws in the United States are a patchwork of federal and state regulations that can be difficult to navigate. Federal laws are enforced by the Federal Trade Commission (FTC), while state laws are enforced by state officials. The FTC has the authority to punish companies for unfair or deceptive practices related to data privacy, and have taken the position that this also applies to data security practices.
At the federal level we have:
- Health Insurance Portability and Accountability Act (HIPAA): This law protects the privacy of individuals' health information.
- Gramm-Leach-Bliley Act (GLBA): This law protects the privacy of individuals' financial information.
- Children's Online Privacy Protection Act (COPPA): This law protects the privacy of children under the age of 13.
And a bunch of others that are specific to certain industries or types of data.
States have also started to pass their own data privacy laws, such as the California Consumer Privacy Act (CCPA) and the New York SHIELD Act. These laws are designed to give consumers more control over their data and to hold companies accountable for data breaches. The state laws vary wildly in their requirements, which makes it tough for companies to stay in compliance.
The Equifax data breach in 2017 and the Cambridge Analytica scandal in 2018 have brought data privacy to the forefront of public consciousness, and have led to many states passing some form of data privacy legislation. More states are expected to follow suit in the coming years, but some just haven't bothered yet.
Without comprehensive federal legislation, companies are left to navigate this patchwork of state laws on their own. This can be a daunting task, especially for small companies that may not have the resources to hire legal experts to help them navigate the regulations.
The safest option is to follow the strictest regulations that apply in the regions where you operate. This will help ensure that you are in compliance with all applicable laws and regulations, and will help protect your company from fines and penalties. This doesn't work when the laws are contradictory, but it's a good starting point.
General Data Protection Regulation (GDPR)
The EU's General Data Protection Regulation (GDPR) is probably the best known and most comprehensive data privacy protections in place today. The full text of GDPR is 261 pages with 99 individual articles and took more than 4 years to create. It outlines how personal data can be handled, the rights that individuals have to their data, and penalties for companies that violate it.
GDPR applies to all companies who do business in the European Union or are storing data about EU citizens. This means that even companies based outside of the EU must comply with GDPR if they are collecting data on EU citizens. The regulation is designed to give individuals more control over their personal data and to hold companies accountable for how they handle that data.

Key Principles
The key principles of GDPR are:
- Lawfulness, fairness, and transparency: Data must be processed lawfully, fairly, and in a transparent manner.
- Purpose limitation: Data must be collected for specified, explicit, and legitimate purposes and not further processed in a manner that is incompatible with those purposes.
- Data minimization: Data must be adequate, relevant, and limited to what is necessary in relation to the purposes for which it is processed.
- Accuracy: Data must be accurate and, where necessary, kept up to date.
- Storage limitation: Data must be kept in a form that permits identification of data subjects for no longer than is necessary for the purposes for which the data is processed.
- Integrity and confidentiality: Data must be processed in a manner that ensures appropriate security of the personal data, including protection against unauthorized or unlawful processing and against accidental loss, destruction, or damage.
- Accountability: The data controller is responsible for demonstrating compliance with the principles of GDPR.
A couple of these points are worth considering in more detail.
Data Minimization
You should identify the minimum amount of personal data you need to fulfill your purpose. You should hold that much information, but no more.
The goal here is to ensure that organizations don't overreach with the type of data that they collect about people. As a software engineer you'll rarely have direct control over what data is collected, but it's worth frequently bringing up the question of any data usefulness. If you don't need it, don't collect it.
Integrity and Confidentiality
Personal data must be protected against unauthorized or unlawful processing, as well as accidental loss, destruction or damage.
GDPR does not actually define what good security practices actually are. Every organization will have different expectations that are based on their industry and the sensitivity of the data they are managing. Generally speaking you should have proper access controls, good credential storage, and encryption where needed. In the event of a data breach, regulators will look into the company's information security setup and determine if fines should be issued.
Accountability
The data controller is responsible for demonstrating compliance with the principles of GDPR.
This is the newest addition to the data protection landscape. It's not enough to just say you're following the rules, you need to be able to prove it. This means having documentation of your data processing activities, data protection impact assessments, and records of consent.
Individual Rights
GDPR also gives individuals a number of rights over their data, including:
- Right to be informed: Individuals have the right to be informed about the collection and use of their personal data.
- Right of access: Individuals have the right to access their personal data and to know how it is being used.
- Right to rectification: Individuals have the right to have inaccurate personal data corrected.
- Right to erasure: Individuals have the right to have their personal data erased.
- Right to restrict processing: Individuals have the right to restrict the processing of their personal data.
- Right to data portability: Individuals have the right to obtain and reuse their personal data for their own purposes.
- Right to object: Individuals have the right to object to the processing of their personal data in certain circumstances.
- Right to withdraw consent: Individuals have the right to withdraw their consent to the processing of their personal data at any time.
Penalties
Companies that violate GDPR can face significant fines, up to 4% of their annual global turnover or €20 million, whichever is greater. This has led to many companies taking data privacy more seriously and investing in data protection measures to avoid fines.

Examples
- British Airways: £183 million fine for a data breach that exposed the personal data of 500,000 customers.
- Marriott International: £99 million fine for a data breach that exposed the personal data of 339 million guests.
- Google: €50 million fine for failing to provide transparent and easily accessible information about its data processing activities.
- La Liga: €250,000 fine for using its mobile app to spy on users by activating their microphones and tracking their location.
- DSK Bank: €511,000 fine for failing to protect the personal data of its customers.
Handling Data
When you do need to handle personal data, beyond the obvious encryption there are a number of techniques for ensuring that it is kept secure and private. These include:
- Aggregation: Combine data into groups to eliminate individual identifiers.
- Pseudonymization: Replace identifying information with artificial identifiers. This keeps the data suitable for analysis without revealing the identity of the individual.
- Anonymization: Remove all identifying information from the data. This is the most secure way to handle data, but it can also limit its usefulness for analysis.
These techniques add a layer of protection to the data and can help reduce the risk personal data being expose because of a data breach. They can also help ensure that data is only used for legitimate purposes and that individuals' privacy is protected by restricting access to the data.
The safest option is to just not collect personal data in the first place. If you don't have the data, you can't lose it. This is not always possible, but it should be the default position when considering what data to collect. Make sure that the data you are collecting has enough value to justify the risk of collecting it.
Conclusion
Data privacy is a complex and evolving field, and it is important for companies to stay up to date on the latest regulations and best practices. Every developer who works with data should be aware of the privacy implications of their work and should take steps to protect the privacy of individuals.
By following best practices and staying informed about the latest regulations, companies can protect their customers' data and avoid costly fines and penalties. Data privacy is not just a legal requirement, it is also a moral imperative. Individuals have a right to privacy, and it is up to companies to respect that right and to protect their data from misuse.